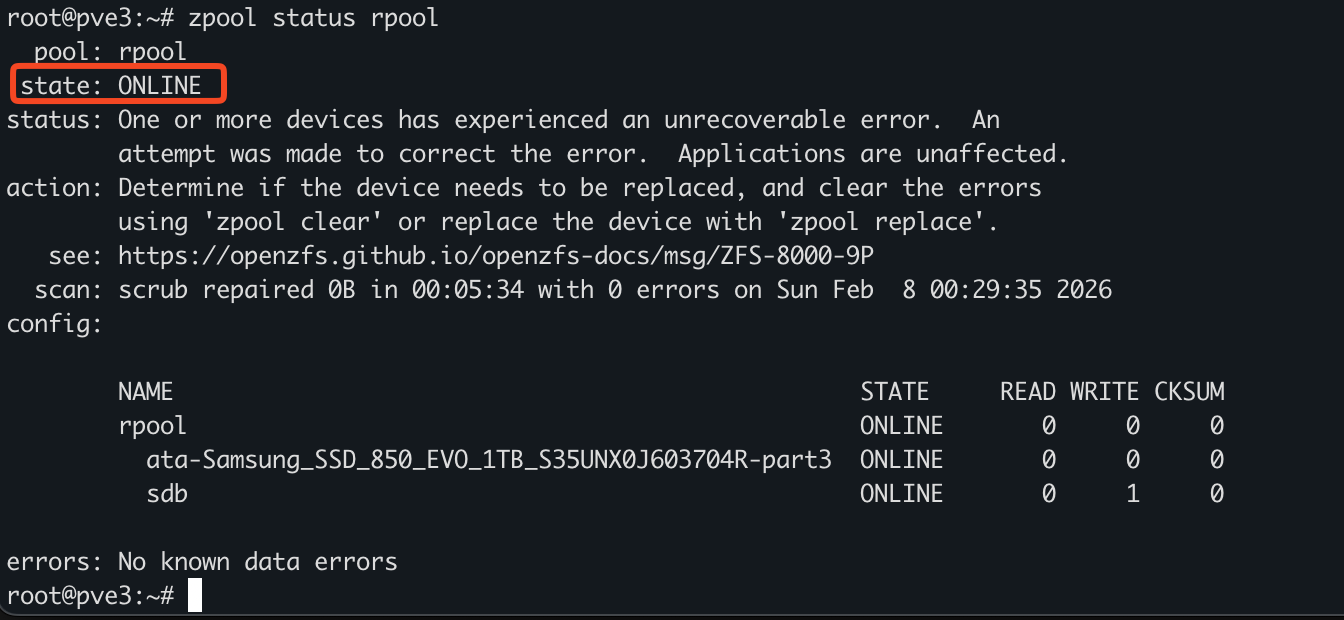
2026-02-21 BJJ Notes
Focus Today I focused on DLR guard, more specifically some of the moves I saw in Jason Rau’s instructional What Worked I like the no-gi grip from DLR, it helps a lot especially when I can’t get upper body controls The foot stomp on the ground to get to the back while in DLR is nice, it makes it easy to dump people Jason Rau’s baby bolo variation where you pinch your top knee in, then use your bottom foot to hook and make space to bring your top leg in for hooks is a nice touch Your browser does not support the video tag. What Failed People are able to flatten their back and shrimp away Against bigger people it’s hard to even play DLR, I’ll need to learn k-guard Key Lessons No-gi style DLR works really well in the Gi Next Session Plan Keep focusing on DLR back takes, the far leg grab and inversion is still loose Look into k-guard