Hey Everyone!
I wanted to share a small (pun intended) improvement to my personal security hygiene.
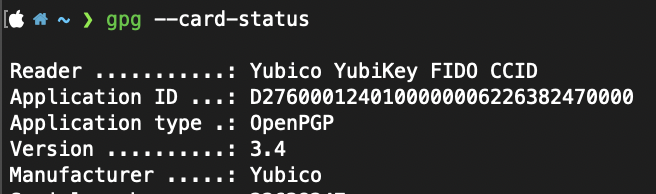
That small improvement is called a YubiKey! For those unaware, a YubiKey is a hardware-based MFA device. It supports an MFA standard known as FIDO2, which is much more secure than TOTP.

I’ve begun implementing this across various applications including my personal email, DNS provider, and even 1Password. The main draw for me is that if any of your authenticator apps are compromised, you are still susceptible to a hack.
The cool thing about having a YubiKey is that I can use it for much more than just MFA; I can also store my GPG and SSH keys for secure access. Currently a lot of those sit in 1Password, but if I was really paranoid I could store them on my hardware key to make sure they are never compromised.
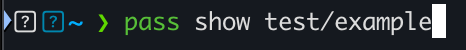
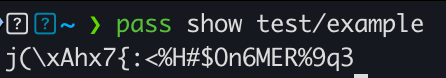
Here is a quick example, I’m using pass which is a simple password manager encrypted using GPG:
I first attempt to retrieve my password, which is encrypted:
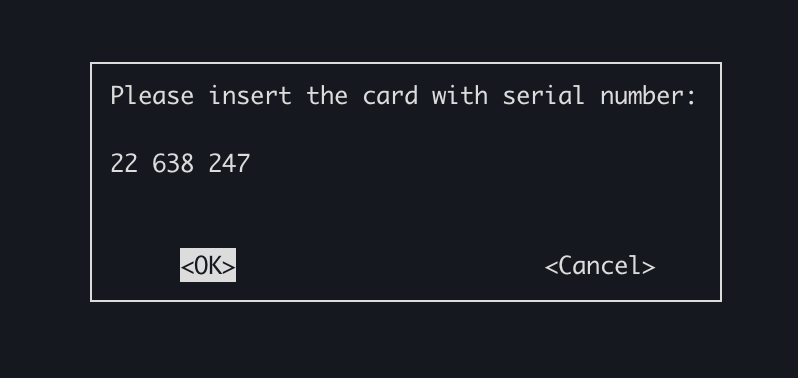
I am then prompted to enter my YubiKey:
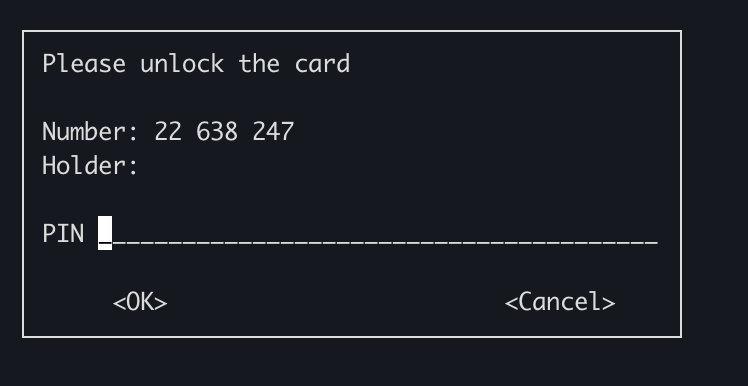
After I enter my YubiKey, it then asks me for an additional PIN:
Then I am able to retrieve my password!
While this is a very basic example, it demonstrates how powerful these keys are. A simple PIN-protected hardware device that contains your private keys that is not accessible via the internet. I don’t even need to explain how secure this makes me theoretically.
Unfortunately for me, my banking apps don’t support these hardware-based keys, many banks don’t even support TOTP, which blows my mind. Regardless, security is not necessarily about crossing the finish line, it’s more about keeping up in the race.