Hey folks,
Quick tip for anybody using DN42. If you’re having an issue making your services reachable on the network you can copy something similar to what I’m doing.
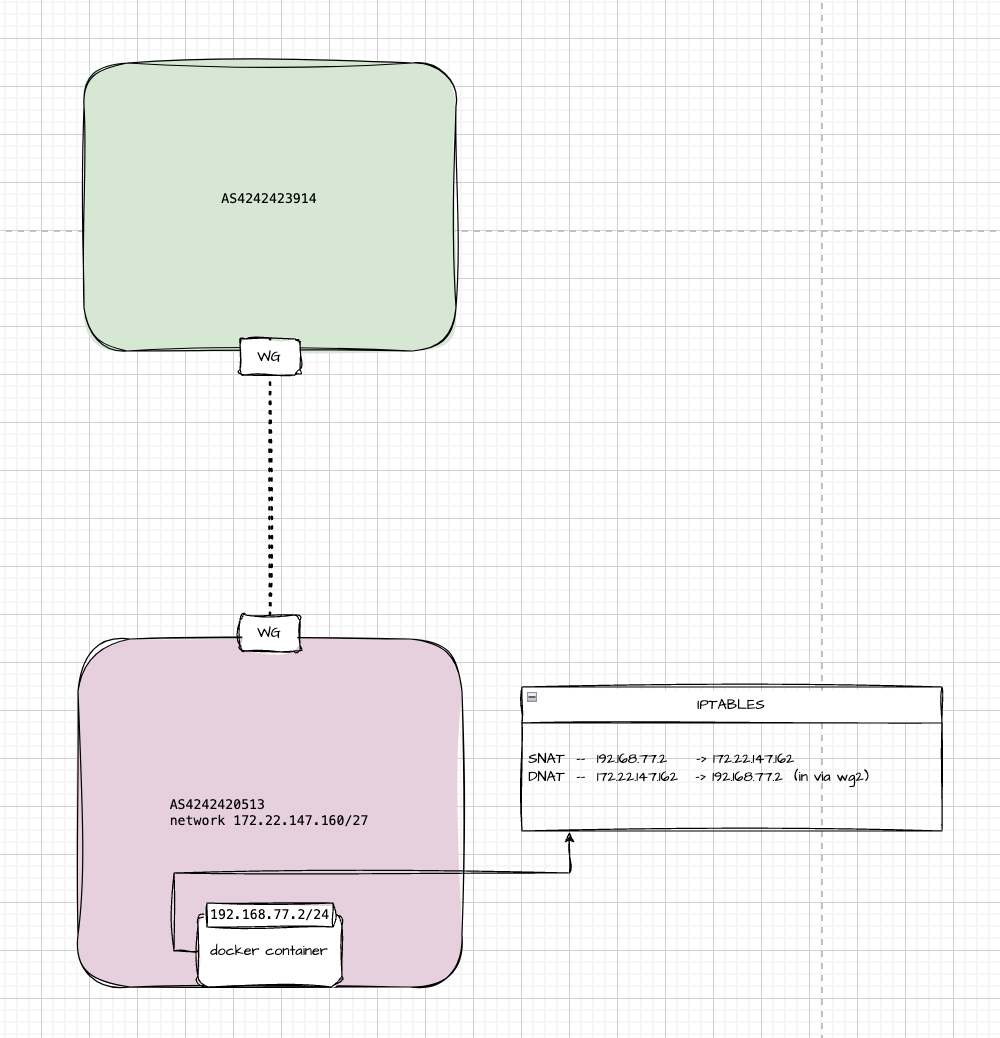
In my lab, I’m running plain Docker, with a container that has a private IP of 192.168.77.2. To make it reachable from a remote peer over WireGuard, I’m using two NAT rules: one for SNAT and one for DNAT.
Why? Because in the DN42 overlay network, only IPs in the 172.20.0.0/14 range are routable. My little slice is 172.22.147.160/27. The whole setup is similar to your home internet with RFC1918 addresses meaning you need to heavily rely on NAT.
Simply put, I just rewrite the packet’s source and destination IPs, and the remote side sees traffic coming from a valid IP in the routable mesh.
Here’s what the iptables rules look like:
# SNAT: outgoing packets from the container
iptables -t nat -A POSTROUTING -s 192.168.77.2 -j SNAT --to-source 172.22.147.162
# DNAT: incoming packets to the routable IP get forwarded to the container
iptables -t nat -A PREROUTING -i wg2 -d 172.22.147.162 -j DNAT --to-destination 192.168.77.2
This allows the container to both send and receive traffic as if it lived on the overlay network.