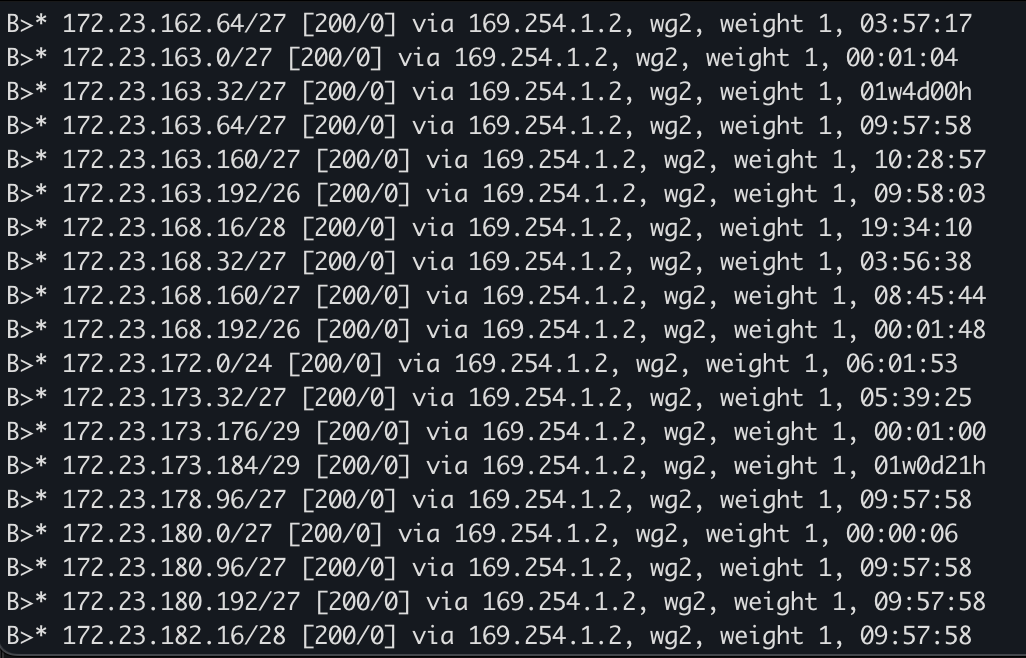
Hi everyone,
If you’re like me, there are tons of technologies that you work with on a day-to-day basis, but never have the opportunity to touch. In my day-to-day role, for example, I work heavily with networking and even with BGP. But rarely do I have the chance to do anything BGP-related as it pertains to the internet.
It’s quite the dilemma! How is one supposed to get the experience of operating large-scale networks, if only very few people have the opportunity to work on them? Let alone set them up from scratch!
Well, the good news is, I have found a solid workaround. It is called DN42. From their homepage, “dn42 is primarily useful for learning routing technologies such as BGP within a reasonably large network (1,500+ ASes, 1,700+ prefixes).”
The idea is simple. You create a private VPN connection (I use WireGuard) and run BGP over that VPN. After that, you find a peer and exchange routes!
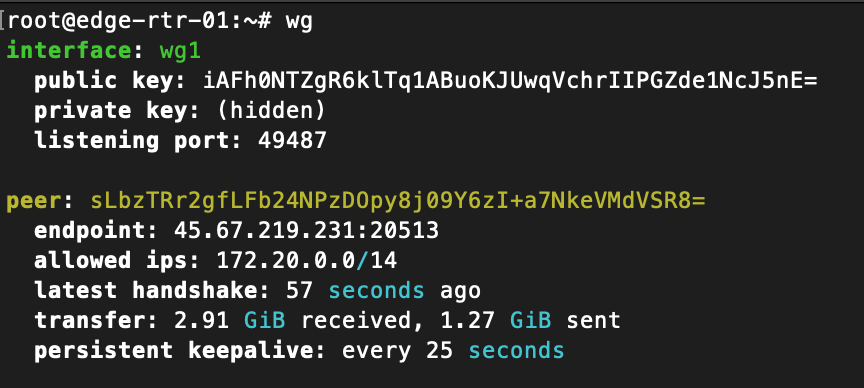
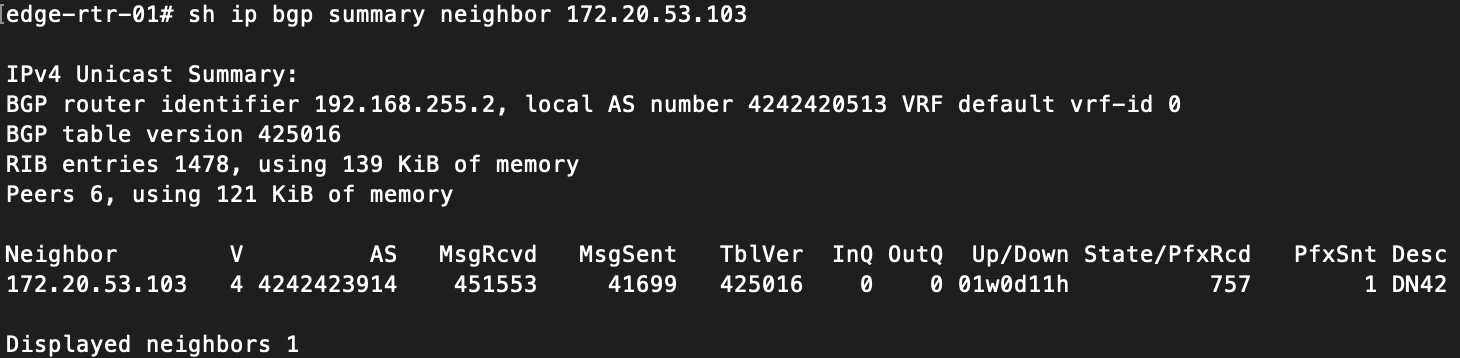
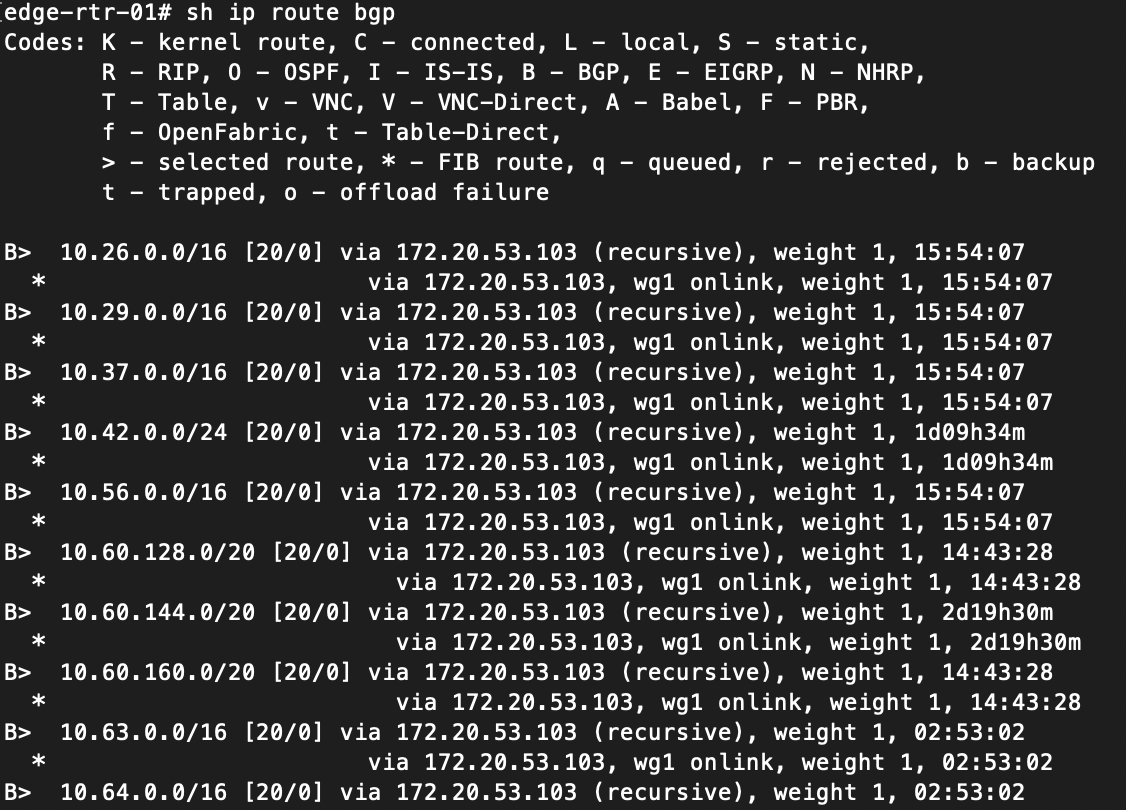
I have two routers that are peered to two different peers in the DN42 intranet (or internet?). They use a configuration similar to below:
frr version 10.0
frr defaults traditional
hostname <ROUTER_HOSTNAME>
log syslog informational
service integrated-vtysh-config
!
debug zebra rib
debug bgp keepalives
debug bgp neighbor-events
debug bgp update-groups
debug bgp updates in
debug bgp updates out
debug bgp zebra
!
router bgp <LOCAL_ASN>
# EDGE-RTR-02
neighbor <EDGE_NEIGHBOR_IP> remote-as <LOCAL_ASN>
neighbor <EDGE_NEIGHBOR_IP> description EDGE-02
neighbor <EDGE_NEIGHBOR_IP> update-source <EDGE_INTERFACE>
neighbor <EDGE_NEIGHBOR_IP> soft-reconfiguration inbound
neighbor <EDGE_NEIGHBOR_IP> route-map set-local-pref-in in
# DN42
neighbor <DN42_NEIGHBOR_IP> remote-as <DN42_ASN>
neighbor <DN42_NEIGHBOR_IP> description DN42
neighbor <DN42_NEIGHBOR_IP> interface <DN42_INTERFACE>
neighbor <DN42_NEIGHBOR_IP> disable-connected-check
neighbor <DN42_NEIGHBOR_IP> soft-reconfiguration inbound
!
address-family ipv4 unicast
network <INTERNAL_NETWORK_1>
network <INTERNAL_NETWORK_2>
neighbor <DN42_NEIGHBOR_IP> route-map dn42 out
exit-address-family
exit
!
access-list dn42 seq 5 permit <INTERNAL_NETWORK_2>
!
route-map set-local-pref-in permit 10
match ip address <INTERNAL_ACCESS_LIST>
set local-preference 200
exit
!
route-map dn42 permit 10
match ip address dn42
exit
!
end
Everything is managed via Ansible, and tracked via git. While this might not be a “real” network, it scales very similarly and there are plenty of other services I can set up. Truth be told, I have not gotten around to setting up other services such as DNS or RPKI, but it is possible. In other words, there is no limit networking-wise to what you can do within DN42.