The mdrfckr SSH Key
On March 29, 2025, my Cowrie SSH honeypot caught something interesting: a known malicious SSH key used by an active botnet campaign.
What Happened
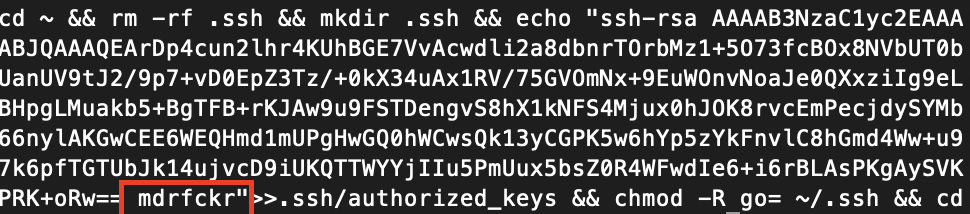
While monitoring my honeypot, I noticed a connection attempt that stood out. After a successful brute-force login (using root credentials), the attacker executed the following command:
cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr" >> .ssh/authorized_keys && chmod -R go= ~/.ssh
The key’s comment field contained the alias: mdrfckr.
Why This Matters
This isn’t just a random attacker — the mdrfckr SSH key is a well-known indicator of compromise (IOC) linked to a long-running malware campaign involving:
- Persistent SSH access via authorized key injection
- Deployment of cryptominers (e.g. XMRig)
- Shellbot (IRC-based backdoor)
- The Outlaw Hacking Group and Dota3 malware family
What is the “mdrfckr” Key?
This exact key — and its comment — has appeared in thousands of honeypot logs across the world. It’s used to maintain access to compromised systems after a brute-force attack.
Researchers have seen this key in use:
- Since at least 2018
- In the Dota3 malware family
- As part of the Outlaw Group’s Shellbot campaigns
- Across thousands of IPs per day
Known Behavior Patterns
- Brute-force login via SSH
- Key injection into authorized_keys
- Dropping crypto miners and IRC bots
- Killing competitor malware
- Persistent access with SSH keys and new users
IOC: The Key Itself
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr
How to Protect Yourself
- Disable password-based SSH logins (PasswordAuthentication no)
- Use SSH key-based authentication
- Monitor .ssh/authorized_keys for unauthorized changes
- Use fail2ban, CrowdSec, or similar tools to block brute-force attacks
- Deploy honeypots to detect and study attacker behavior in real time
Conclusion
Catching the mdrfckr key in my honeypot was a great reminder that automated botnets are still alive and well, scanning for weak SSH setups and quickly deploying persistence mechanisms. Running Cowrie not only lets you observe this activity safely, it arms you with real-world intel that others can benefit from.
Resources & Further Reading
- Yoroi Threat Report: Outlaw Group
- Juniper Networks: Dota3 Malware
- Honeypot Diaries: Michael Edie
- Cowrie Honeypot GitHub
Stay curious - Will